With Musical Cryptography, Composers Can Hide
Messages in Their Melodies
By mapping notes to letters, some musicians
sneak secret
words into tunes.
OUT OF THE MANY TROPES in TV and literature, espionage is one that spurs drama and intrigue for viewers and readers alike. A budding protagonist wants to convey a secret message in a letter or text, but must scramble the message so discreetly to avert the eager antagonist’s gaze. Will the message send through securely? The suspense always deadly.
One unexpected form of transmitting such messages is through music. It’s better known as music cryptography, which is a method in which the musical notes A through G are used to spell out words, abbreviations, or codes.
This secret writing appears as a plot point in TV shows such as Outlander, the 18th-century time travel drama based in Scotland, and mystery novels like the Secret of the White Rose, which features characters who employ music ciphers as undetectable modes of espionage or communication.
In the season two Outlander episode “Useful Occupations and Deceptions,” for example, the protagonists, Jamie and Claire, intercept a letter from Prince Charles Edward Stuart that also includes a page of German sheet music sent from England. The clumsy music contains almost the same melodies as Bach’s “Goldberg Variation,” but with five random key changes, which according to the virtuoso nun who played the music, is more than usual. When deciphered by Jamie, the sharps and flats in the musical keys reveal a message that Prince Stuart intends to start a war to reclaim his throne using 40,000 pounds from Jamie and Claire’s nemesis the Duke of Sandringham, and few other English conspirators. This persuasive scenario makes one wonder if music cryptography is a real spy technique.
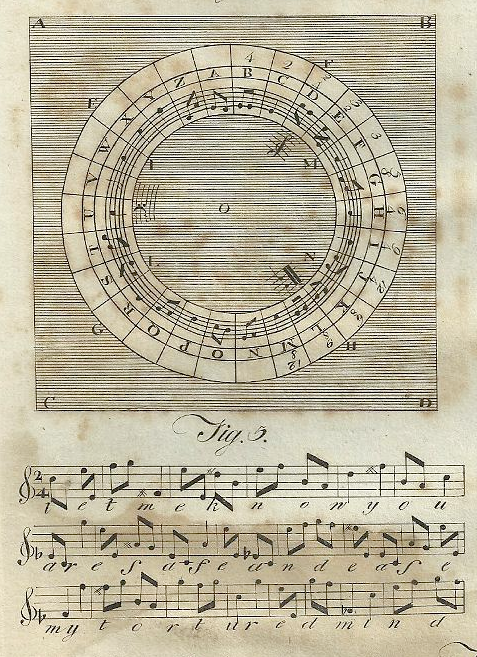
Early 17th- and 18th-century mathematicians and cryptologists such as John Wilkinsand Philip Thicknesse argued that music cryptography was one of the most inscrutable ways of transporting secret messages. They claimed that music was perfect camouflage, because spies would never suspect music. When played, the music would sound so much like any other composition that musically trained listeners would be easily fooled, too. Thicknesse wrote in his 1772 book A Treatise on the Art of Deciphering, and of Writing in Cypher: With an Harmonic Alphabet, “for who that examined a suspected messenger would think an old song, without words, in which perhaps the messenger’s tobacco or snuff might be put, contained a secret he was to convey?” Written letters don’t have this advantage.

He added, “I am persuaded an alphabet of musical notes may be so contrived, that the notes shall not only convey the harmony, but the very words of the song, so that a music-master … may instruct his female pupil, not only how to play upon an instrument, but how to play the fool at the same time.”
Thicknesse created an enciphering system that employs quarter and half notes with treble clef and key signature. He claimed his harmonic alphabet ensured strong encryption and expressed the words “perfectly to the eye as they do the harmony to the ear.” He also wrote of English philosopher Francis Bacon’s music cipher technique, in which a particular number of the notes A or B equate to each alphabet letter (aaaaa translates to A), “the above method of secret writing is certainly the most ingenious of any ever invented.”
It is highly likely that messages using codes like these would go undetected, at least to an untrained eye and ear. To a trained eye, however, says Western Michigan University Music Professor David Loberg Code, a sequence of notes with a message hidden inside might provoke questions. “Since their encryption system is not musical, the manuscript would look suspicious because it contains musical nonsense,” he says. If someone were to send music theorist Michael Haydn’s 26-note motif, in which the lower bass clef G translates to A, then G sharp equals B, and so forth, isolated on its own music sheet, the motif would look disjointed. When played, it might sound dreadfully boring in style or like a random, atonal string of pitches, says Code.
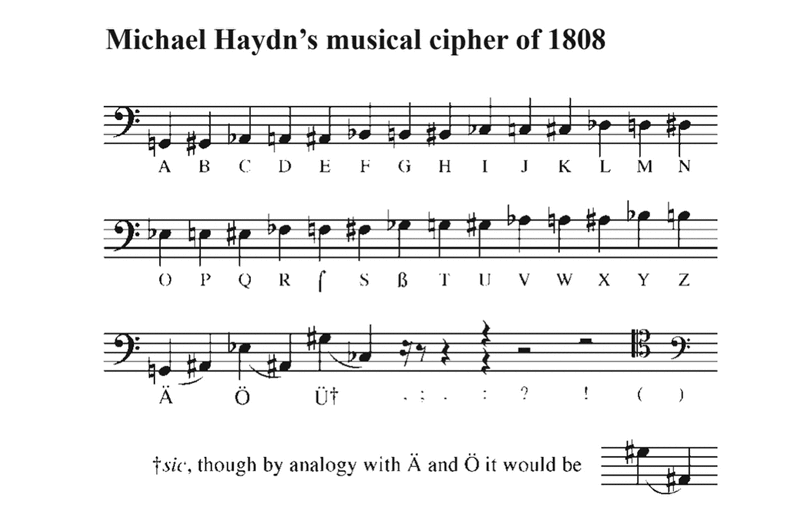
The prime users of musical encryption were classical composers, but there are no known examples of the technique being used for espionage or intelligence purposes. Rather, most composers put the letters of their name or a friend’s into compositions simply because it was fun.
“Sometimes a musical version of a name is a subtle reference in the piece of music,” Code says. “Often it is very prominent; it is the main theme of the piece and is heard over and over. In that case, whether or not you know exactly how the composer translated the name into musical pitches, it is obvious that it is meant to be heard.” These composers wanted to leave a traces of themselves, and they “were not secretive about it; they wrote about [it] or told people what they were doing.” They didn’t mind if interested onlookers found their cryptograms.
One well-recognized music cipher comes from the 19th-century German composer Johannes Brahms. He included a cryptogram in his 1868 “String Sextet No. 2 in G major.” In the summer of 1858, a 25-year-old Brahms fell madly in love with Agathe von Siebold, a 23-year-old music director and vocal student of Brahms’s friend Julius Otto Grimm. They quickly set plans for marriage, but in January 1859, he broke off the engagement to focus on his music.
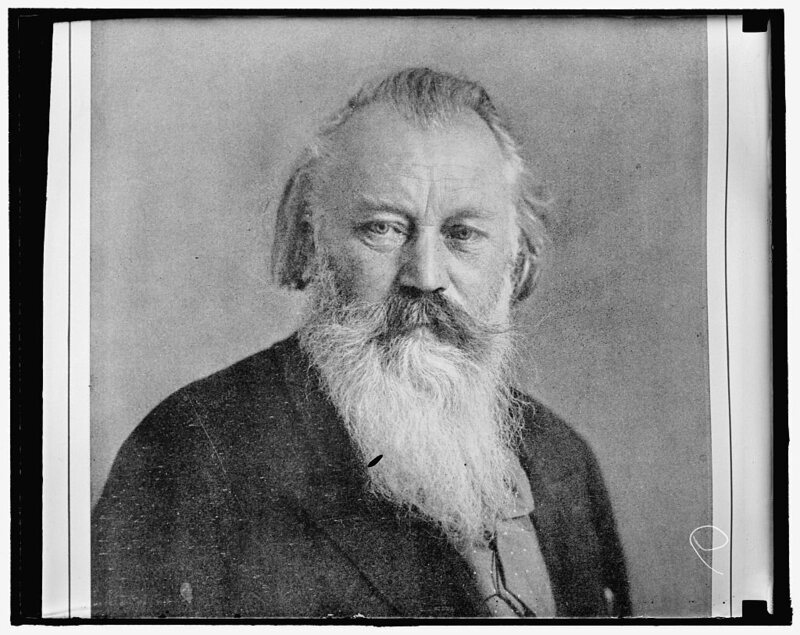
Von Siebold later married, and Brahms remained a bachelor until death, but he still longed for her. He incorporated the notes A-G-A-H-E in bars 162 to 168 in the first movement of his sextet. (B-natural in German nomenclature is the note H; the letter T is not included because it is not a musical note.)
According to BBC radio host Tom Service, the motif is played at the piece’s “greatest and most aching release,” likely signaling Brahms’s heartache. In a letter to his friend Josef Gänsbacher about the sextet, Brahms wrote, “by this work, I have freed myself of my last love.”
Well before Brahms’s time, the prodigious Johann Sebastian Bach spelled out his own name in compositions using a succession of the notes B-A-C-H (B-natural). This short music monogram is now called a Bach motif, and Bach wove his name in various pieces such as his final work, “The Art of Fugue.”
Brahms’ close friend and Romantic-era composer Robert Schumann also integrated music cryptograms into his compositions. Schumann placed the cryptograms, A-S-C-H, A-s-C-H, and S-C-H-A in his piece, “Carnaval.” (In German nomenclature, E flat equates to S and A flat equates to As.) The three codes represent the name of his then fiancé’s birthplace of Asch, Germany, (now in Czechia). The second is the German spelling of ash to honor the Christian holy day of Ash Wednesday. The final cryptogram is selected letters from his name.

Even as musical styles evolved in the 20th century, music composers such as Joseph Maurice Ravel, Achille-Claude Debussy, Francis Poulenc, Olivier Messiaen, and Dmitri Shostakovich continued experimenting with musical motifs, some up to 26 notes, to spell out their names in compositions.
French composer Olivier Messiaen’s cipher, which matches a different note for all 26 letters in the alphabet, created words that sounded similar to his organ work “Méditations sur le mystère de la Sainte Trinité.” Code says the notes deciphered translated to the French words from Summa Theologica by philosopher Thomas Aquinas for essence, humankind, paternity, and illumination. Known for his rich tones and complex rhythms, Messiaen was one of the few to develop a cipher that closely mirrored his own style.
WHAT IF YOU WANT TO create your own composition with a hidden message or a shout-out to a friend? It’s possible. Code has developed a site called Solfa Cipher that turns text into singable melodies. Rather than use 26 different pitches for each letter of the alphabet, “Solfa Cipher maps letters onto only seven notes of a musical scale (Do, Re, Mi, Fa, Sol, La, Ti) combined with unique durations,” says Code. The site also includes a decoding grid and tool.
If you’re more interested in cracking codes, there are cryptography groups that exist, too. Last year, some professional and student cryptanalysts met at an applied cyber-security contest and event called NorthSec conference in Montreal, Canada. Among the challenges created by NorthSec, an encoded Solfa Cipher, which the attendants solved using an encryption key that is defined by four elements: a clef, a tonic, a mode, and a rhythmic unit. In his blog Infected Packages, attendee Jonathan Racicot wrote that participants then translated using a English language translation matrix. The message read: “The first half of the flag is the word subdermal. Concatenate with the second half to obtain a complete flag. Glory to Rao.”
Whether a musical cipher encodes a composer’s name or a more complex message like the above, for most music theorists and cryptographers, decrypting is not always the desired trophy. Sometimes the thrill is knowing that the music holds intricate patterns and meaning that are beyond deciphering.
No comments:
Post a Comment